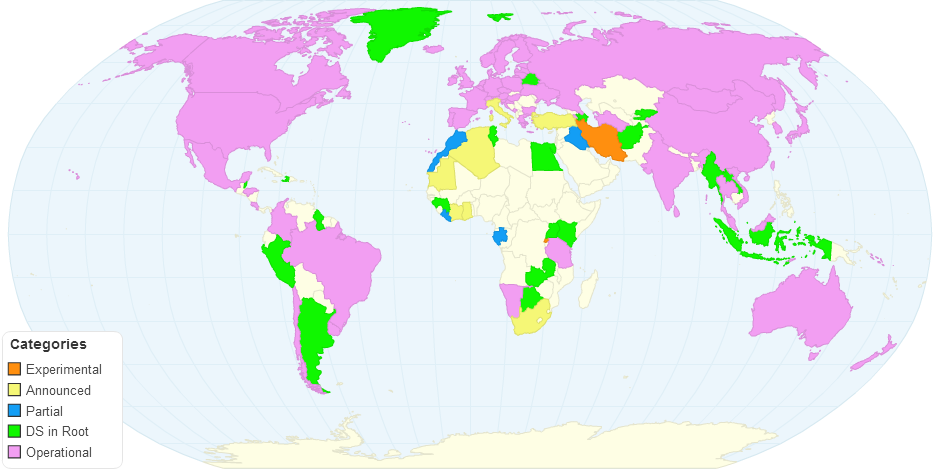
This chart shows the DNSSEC Deployment Status on 25-01-2016.
The maps provide a view into global DNSSEC deployment and break the deployment status of top-level domains (TLDs) out into the following five categories:
1.Experimental – Internal experimentation announced or observed.
2.Announced – Public commitment to deploy.
3.Partial – Zone is signed but not in operation (no DS in root).
4.DS in Root – Zone is signed and its DS has been published.
5.Operational – Accepting signed delegations and DS in root.
These are a bit different from other DNSSEC statistics sites in that they contain both factual, observed information and also information based on news reports, presentations and other collected data.These are produced by the Internet Society Deploy360 Programme based on a database and programs originally.
The Domain Name System Security Extensions (DNSSEC) is a suite of Internet Engineering Task Force (IETF) specifications for securing certain kinds of information provided by the Domain Name System as used on Internet Protocol networks. It is a set of extensions to DNS which provide to DNS clients origin authentication of DNS data, authenticated denial of existence, and data integrity, but not availability or confidentiality.
DNSSEC introduces the ability for a hostile party to enumerate all the names in a zone by following the NSEC chain. NSEC RRs assert which names do not exist in a zone by linking from existing name to existing name along a canonical ordering of all the names within a zone. Thus, an attacker can query these NSEC RRs in sequence to obtain all the names in a zone. Although this is not an attack on the DNS itself, it could allow an attacker to map network hosts or other resources by enumerating the contents of a zone.
10 years ago